The Onion Root
Tor (the onion root) makes it more difficult for Internet activity to be traced back to the user. This includes visits to Web sites, online posts, instant messages, and other communication forms. Tor's use is intended to protect the personal privacy of users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities from being monitored.
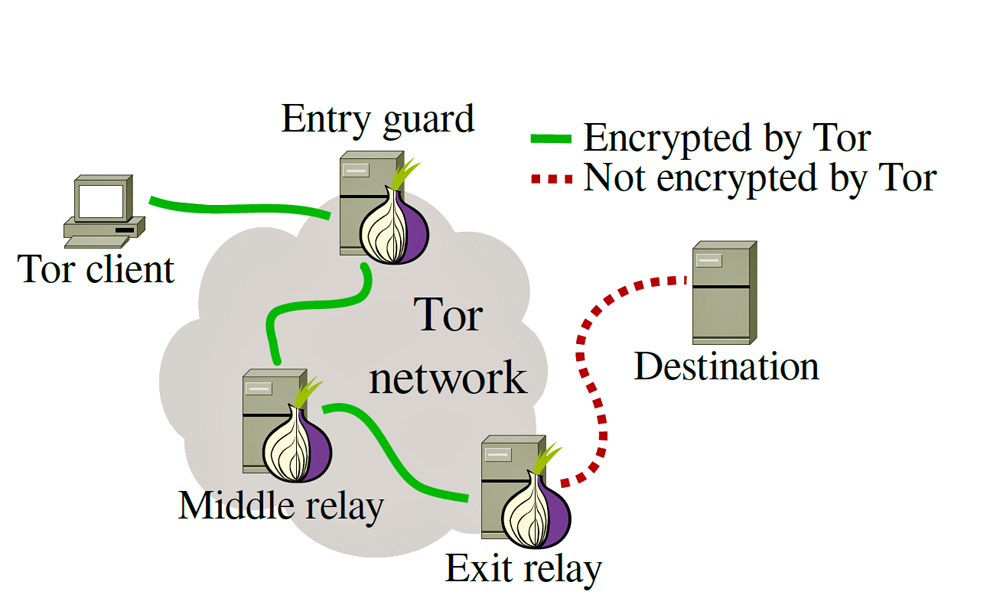
Onion routing is implemented by encryption in the application layer of a communication protocol stack, nested like the layers of an onion. Tor encrypts the data, including the next node destination IP address, multiple times and sends it through a virtual circuit comprising successive, randomly selected Tor relays. Each relay decrypts a layer of encryption to reveal only the next relay in the circuit in order to pass the remaining encrypted data on to it. The final relay decrypts the innermost layer of encryption and sends the original data to its destination without revealing, or even knowing, the source IP address. Because the routing of the communication is partly concealed at every hop in the Tor circuit, this method eliminates any single point at which the communicating peers can be determined through network surveillance that relies upon knowing its source and destination.
Onion routing is implemented by encryption in the application layer of a communication protocol stack, nested like the layers of an onion. Tor encrypts the data, including the next node destination IP address, multiple times and sends it through a virtual circuit comprising successive, randomly selected Tor relays. Each relay decrypts a layer of encryption to reveal only the next relay in the circuit in order to pass the remaining encrypted data on to it. The final relay decrypts the innermost layer of encryption and sends the original data to its destination without revealing, or even knowing, the source IP address. Because the routing of the communication is partly concealed at every hop in the Tor circuit, this method eliminates any single point at which the communicating peers can be determined through network surveillance that relies upon knowing its source and destination.
Tor can also provide anonymity to websites and other servers. Servers configured to receive inbound connections only through Tor are called hidden services. Rather than revealing a server's IP address (and thus its network location), a hidden service is accessed through its onion address, usually via the Tor Browser.
How to install in windows?
Warning: Install tor only from tor official website (https://www.torproject.org)
2. Click on download Tor on home page.
3. Click on download button.
4. After downloading click on downloaded file and install tor.
5. After installing tor network settings will open and click on connect.
6. Enjoy Tor browsing.
Note: Tor browser is self contained; you cannot see any file outside tor icon. Just delete the tor folder and you are done with that.
Do’s and don’ts over Tor
1. Don’t never ever use Google
Yes, you should not use Google to search the Internet if you care for your privacy. Google is known for collecting information on users’ browsing and search data to facilitate the growth of its ads revenue. Also it collects user’s location which might create problem if you want to go anonymous.
You should consider using alternatives DuckDuckGo. DuckDuckGo is default search engine on Tor. It does not save your search results and your location also. The site uses a syndication model that keeps your info private.
2. Don’t torrent over Tor
Torrent file-sharing applications have been observed to ignore proxy settings and make direct connections even when they are told to use Tor. Even if your torrent application connects only through Tor, you will often send out your real IP address in the tracker GET request, because that's how torrents work. Not only do you deanonymize your torrent traffic and your other simultaneous Tor web traffic this way, you also slow down the entire Tor network for everyone else.
3. Don't enable or install browser plug-in
Tor Browser will block browser plug-in such as Flash, RealPlayer, Quicktime, and others. They can be manipulated into revealing your IP address. Similarly, we do not recommend installing additional add-ons or plug-in into Tor Browser, as these may bypass Tor or otherwise harm your anonymity and privacy.
4. Don't open documents downloaded through Tor while online
Tor Browser will warn you before automatically opening documents that are handled by external applications. DO NOT IGNORE THIS WARNING. You should be very careful when downloading documents via Tor (especially DOC and PDF files, unless you use the PDF viewer that's built into Tor Browser) as these documents can contain Internet resources that will be downloaded outside of Tor by the application that opens them. This will reveal your non-Tor IP address.
5. Use HTTPS versions of websites
Tor will encrypt your traffic to and within the Tor network, but the encryption of your traffic to the final destination website depends upon on that website. To help ensure private encryption to websites, Tor Browser includes HTTPS Everywhere to force the use of HTTPS encryption with major websites that support it. However, you should still watch the browser URL bar to ensure that websites you provide sensitive information to display a blue or green URL bar button, include https:// in the URL, and display the proper expected name for the website. Also see EFF's interactive page explaining how Tor and HTTPS relate.
6. Use bridges and/or find company
Tor tries to prevent attackers from learning what destination websites you connect to. However, by default, it does not prevent somebody watching your Internet traffic from learning that you're using Tor. If this matters to you, you can reduce this risk by configuring Tor to use a Tor bridge relay rather than connecting directly to the public Tor network. Ultimately the best protection is a social approach: the more Tor users there are near you and the more diverse their interests, the less dangerous it will be that you are one of them. Convince other people to use Tor, too!
7. Don’t use TOR with Windows
Microsoft’s Windows is the world’s most used operating system for desktops, but it doesn’t seem to do well when you would like to use TOR browser on it. The credits are bagged by the vulnerabilities that exist on the operating system and may reveal your identity even if you are using the TOR to access the internet. Linux systems will serve you well for this purpose. Linux distributions like Tails and Whonix are pre-configured with TOR. You can configure it manually on any distribution you may like. If using tor on windows then keep your windows updated.
Finally, by installing tor you may be on the eye of government agencies, hackers however 100% anonymity is not possible. Still there are chances for someone to hack. If Tor can’t be hacked, then your computer can be. Hackers or agencies can install Trojans or malwares, they can get every information you type or hack your monitor screen. That’s why windows are so vulnerable to these kinds of attacks. So, considering all above mentioned maybe because you just want to be a Pseudonymous for a while, or you are an activist who wants to spread some information, or you’re being followed on the internet. TOR is there for you, you only have to learn how to use it efficiently, and you’ll start loving the digital world.



Comments
Post a Comment